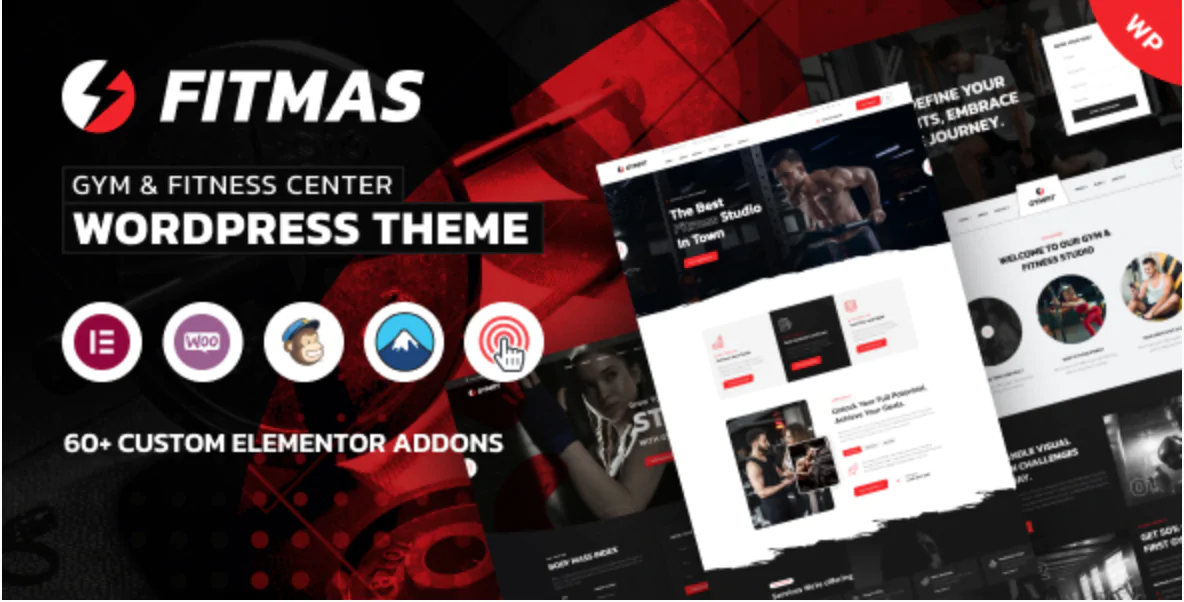
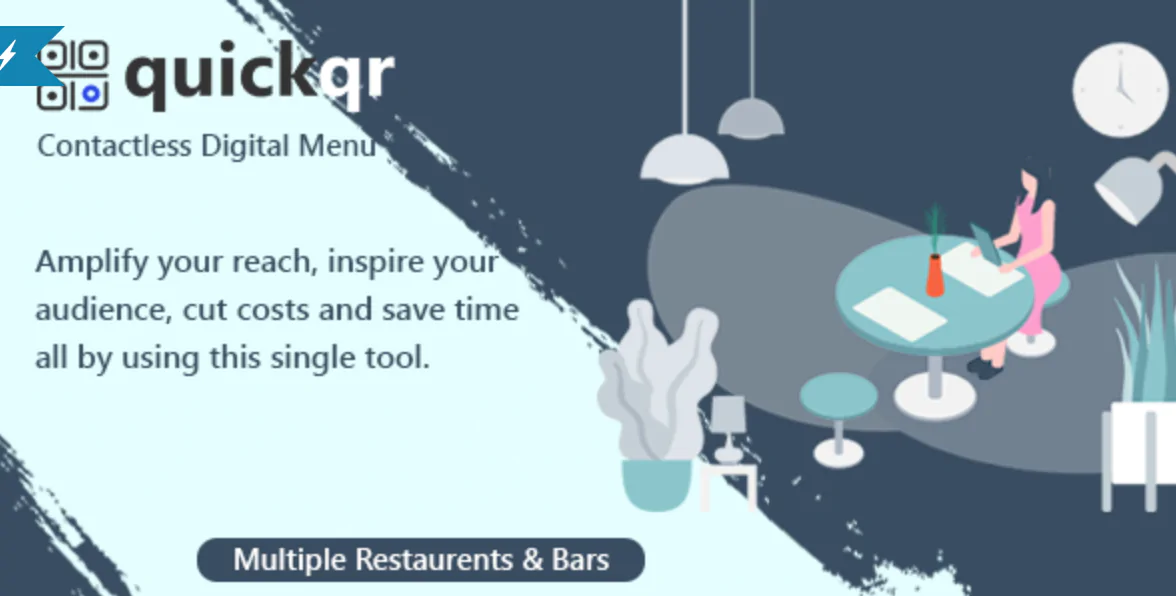
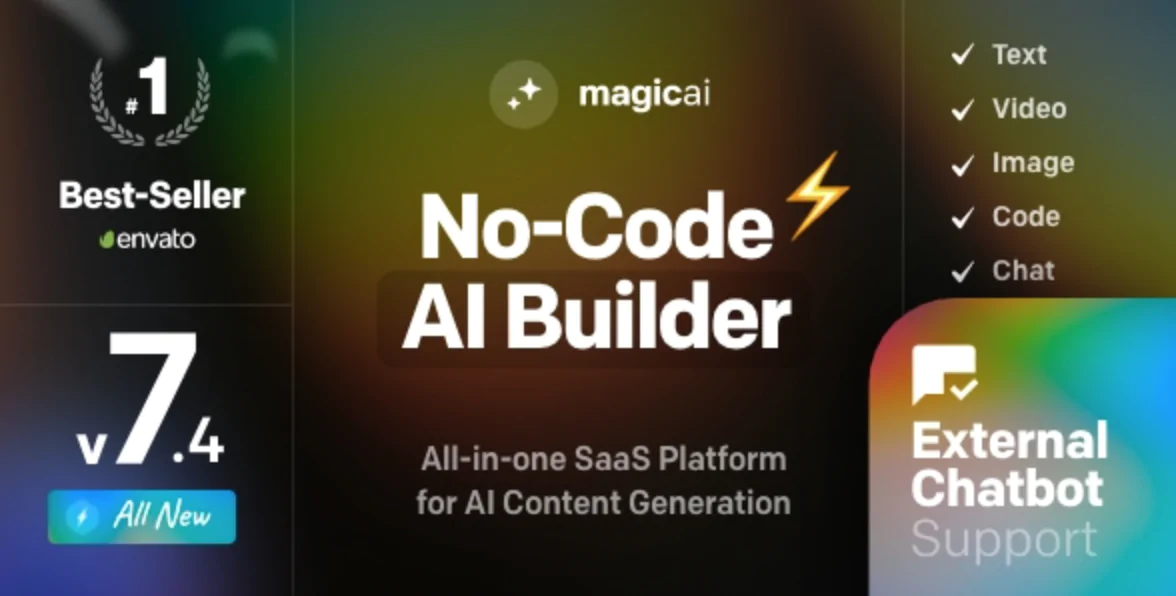
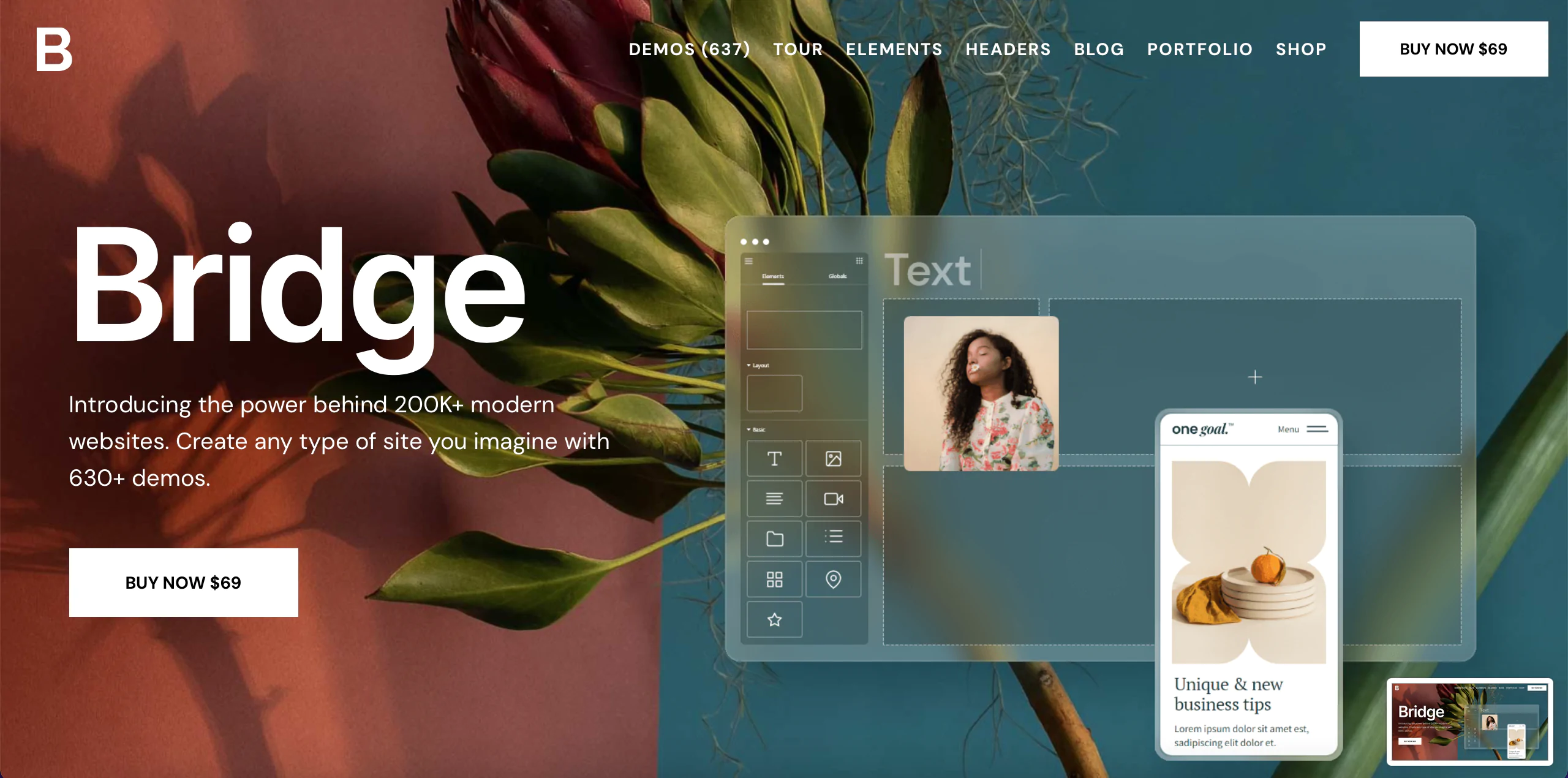
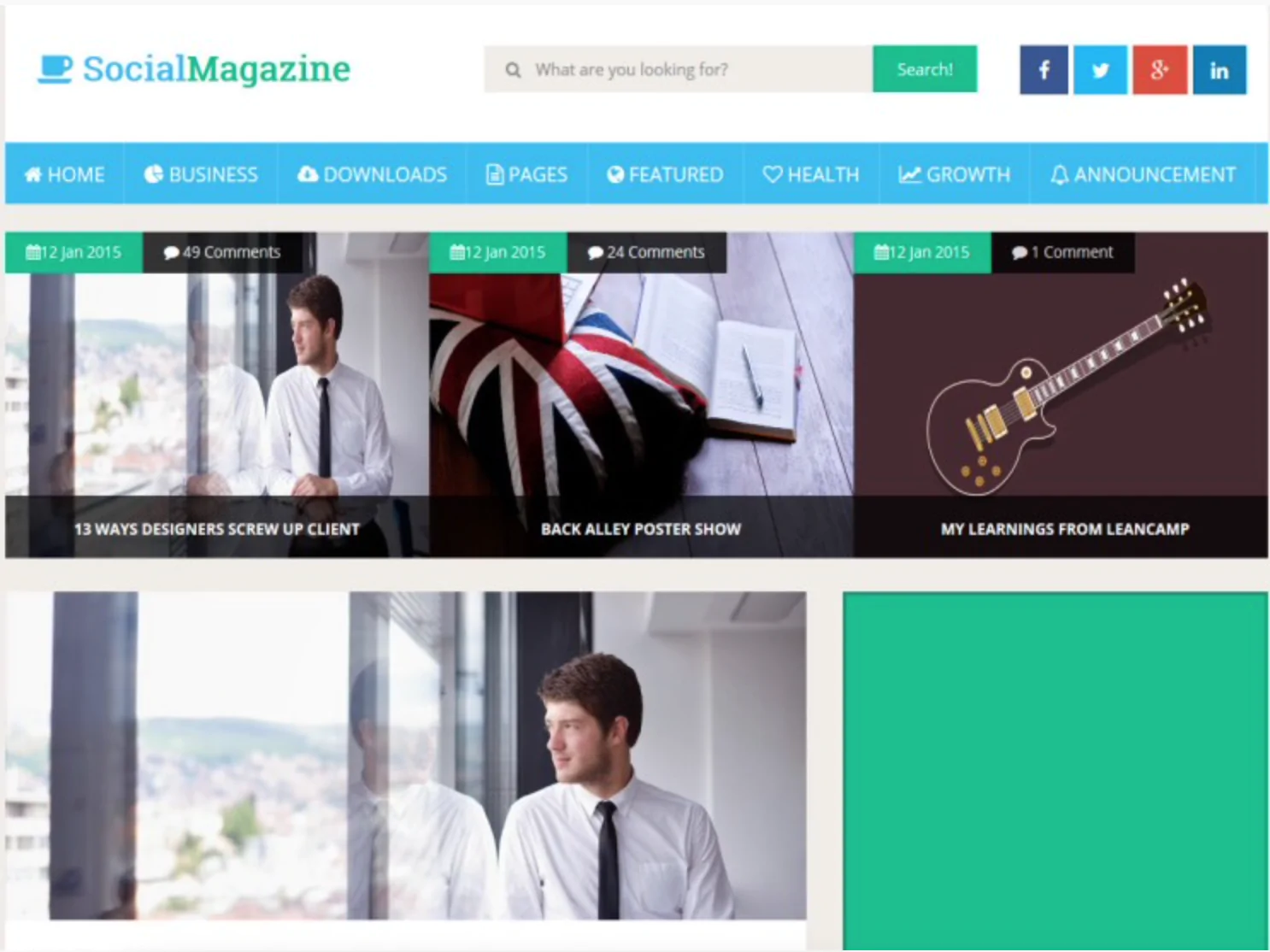
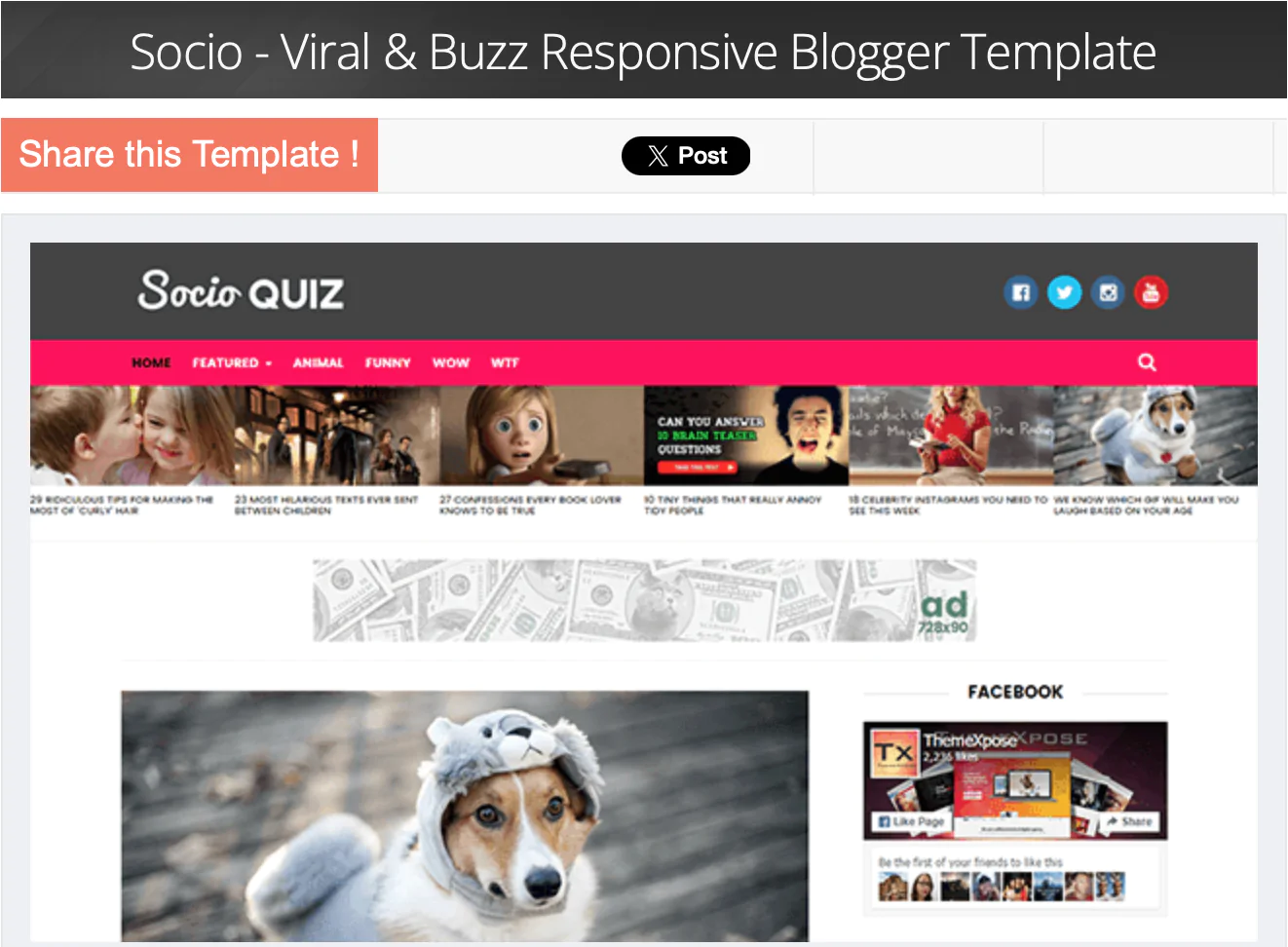
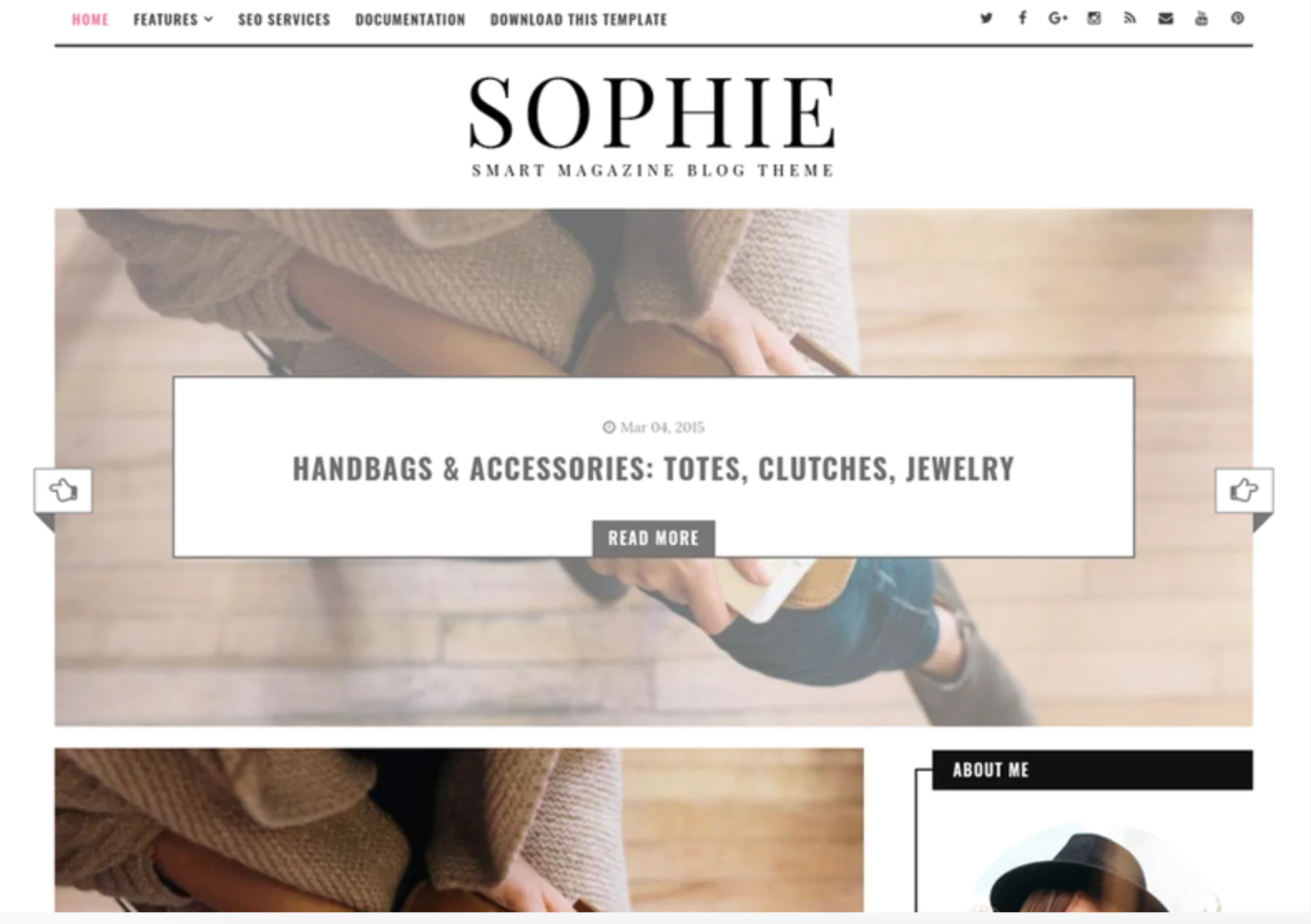
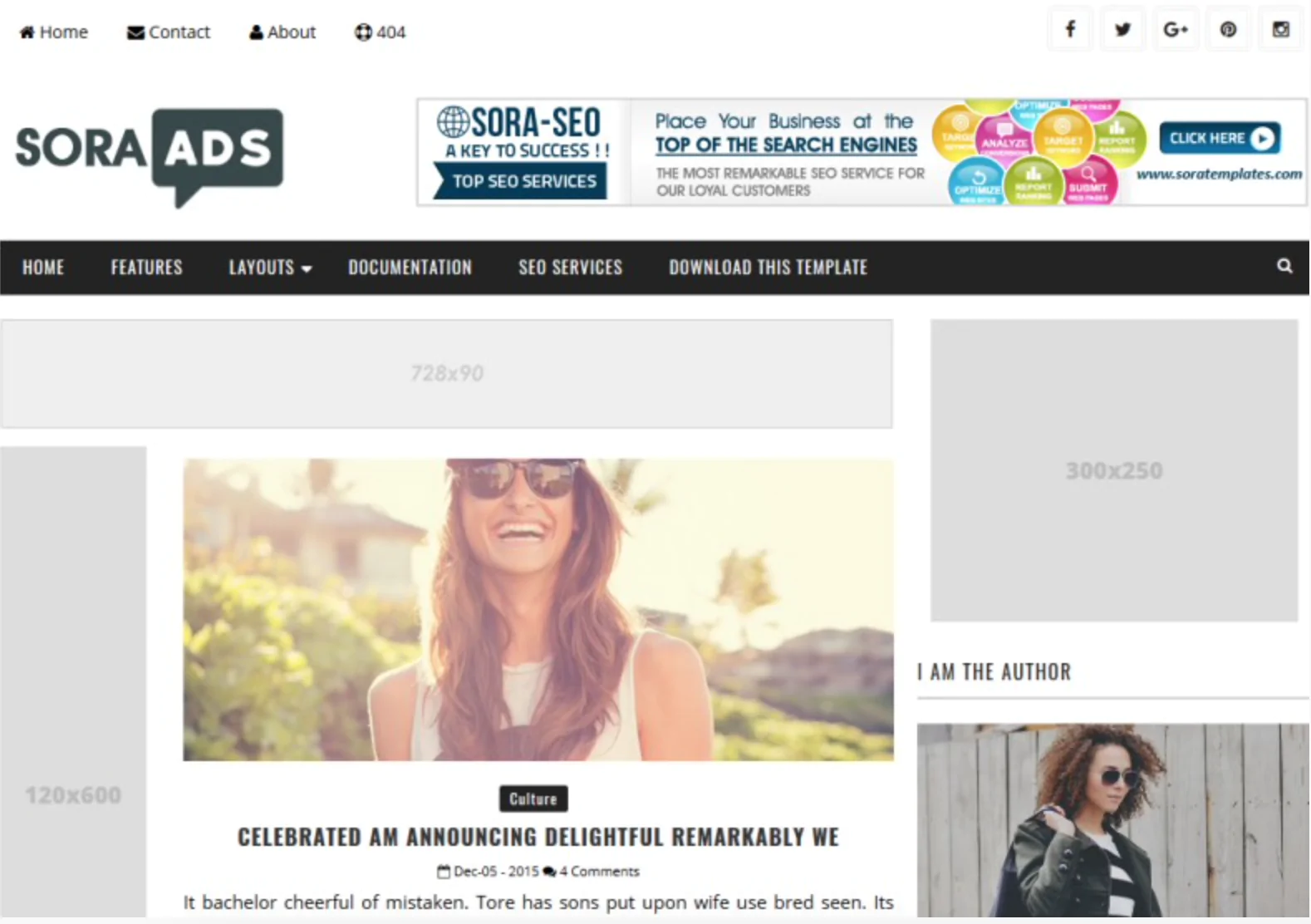
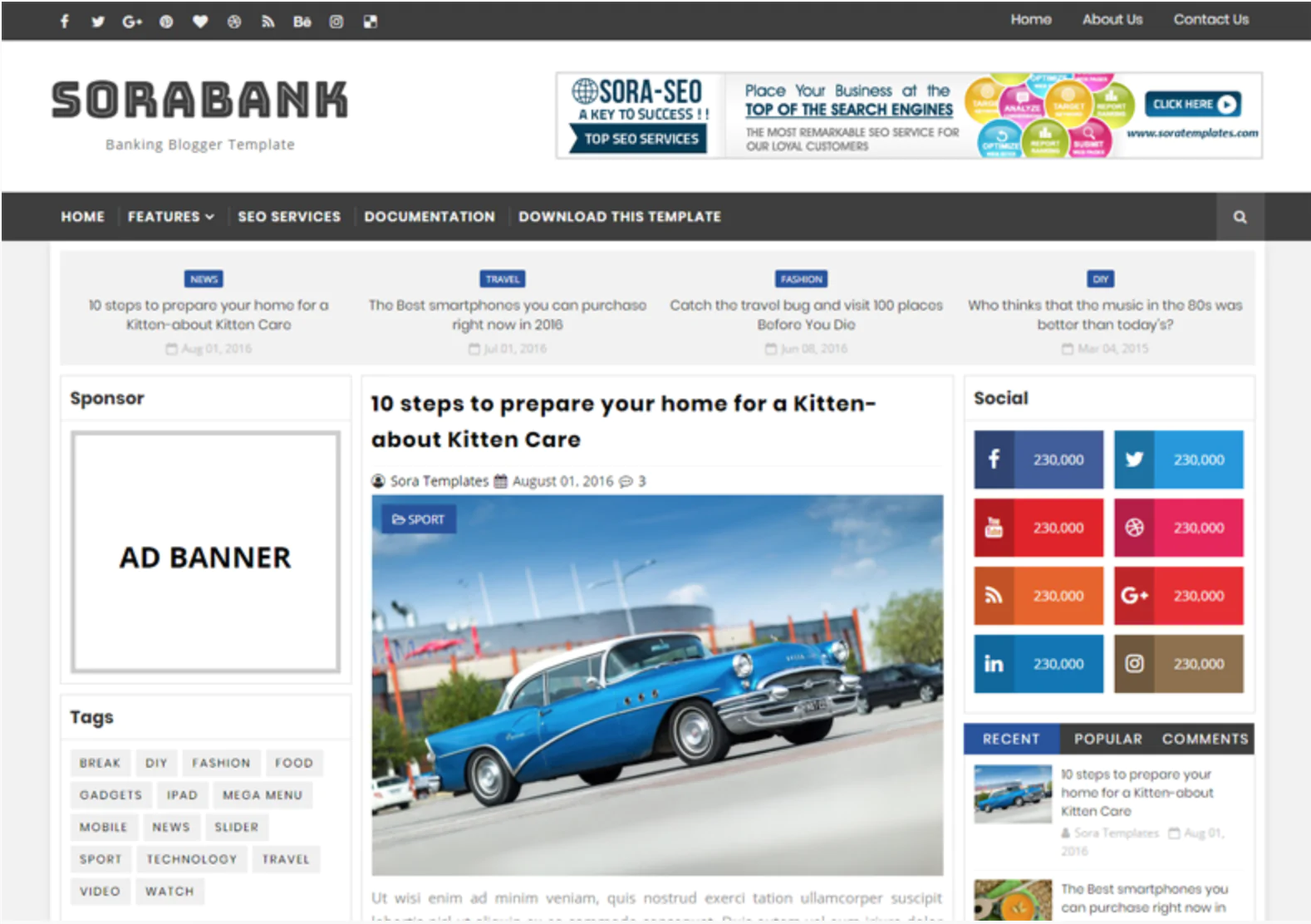
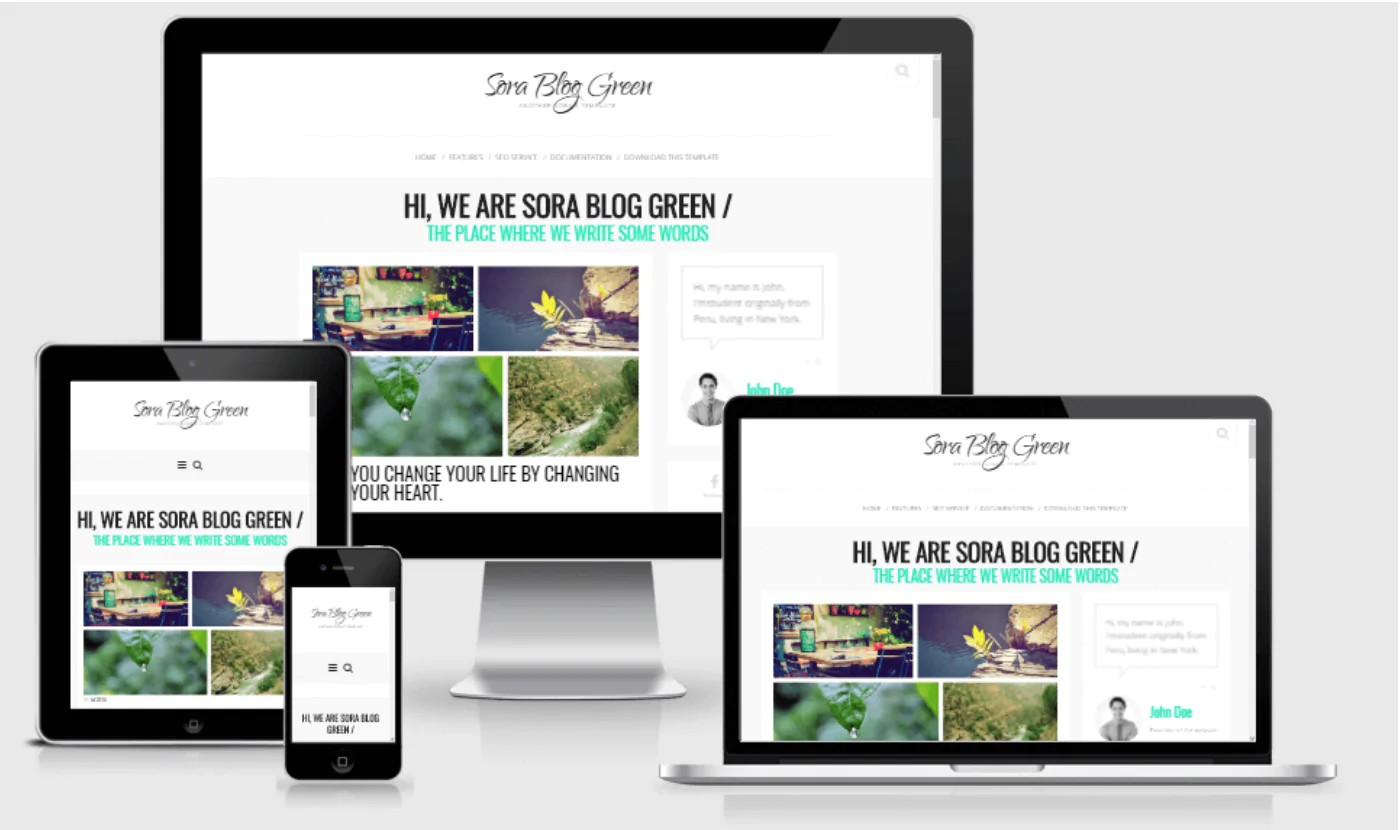
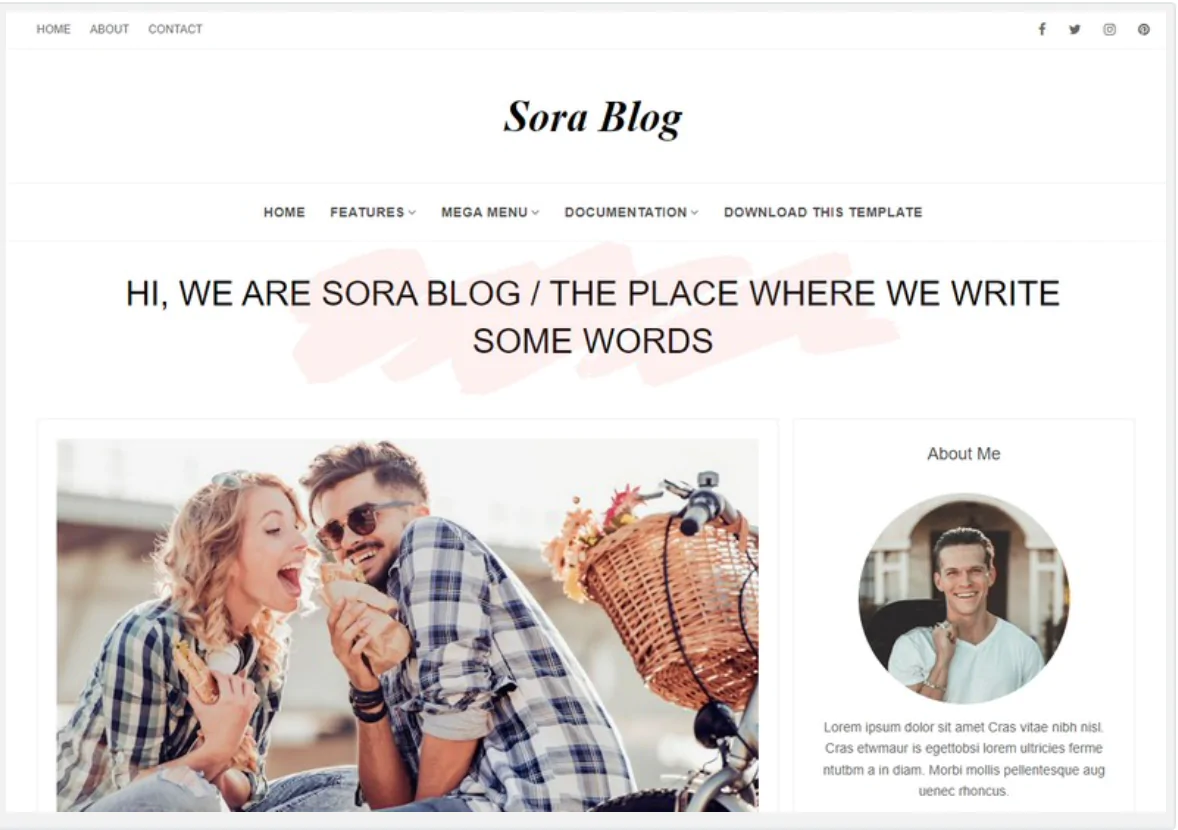
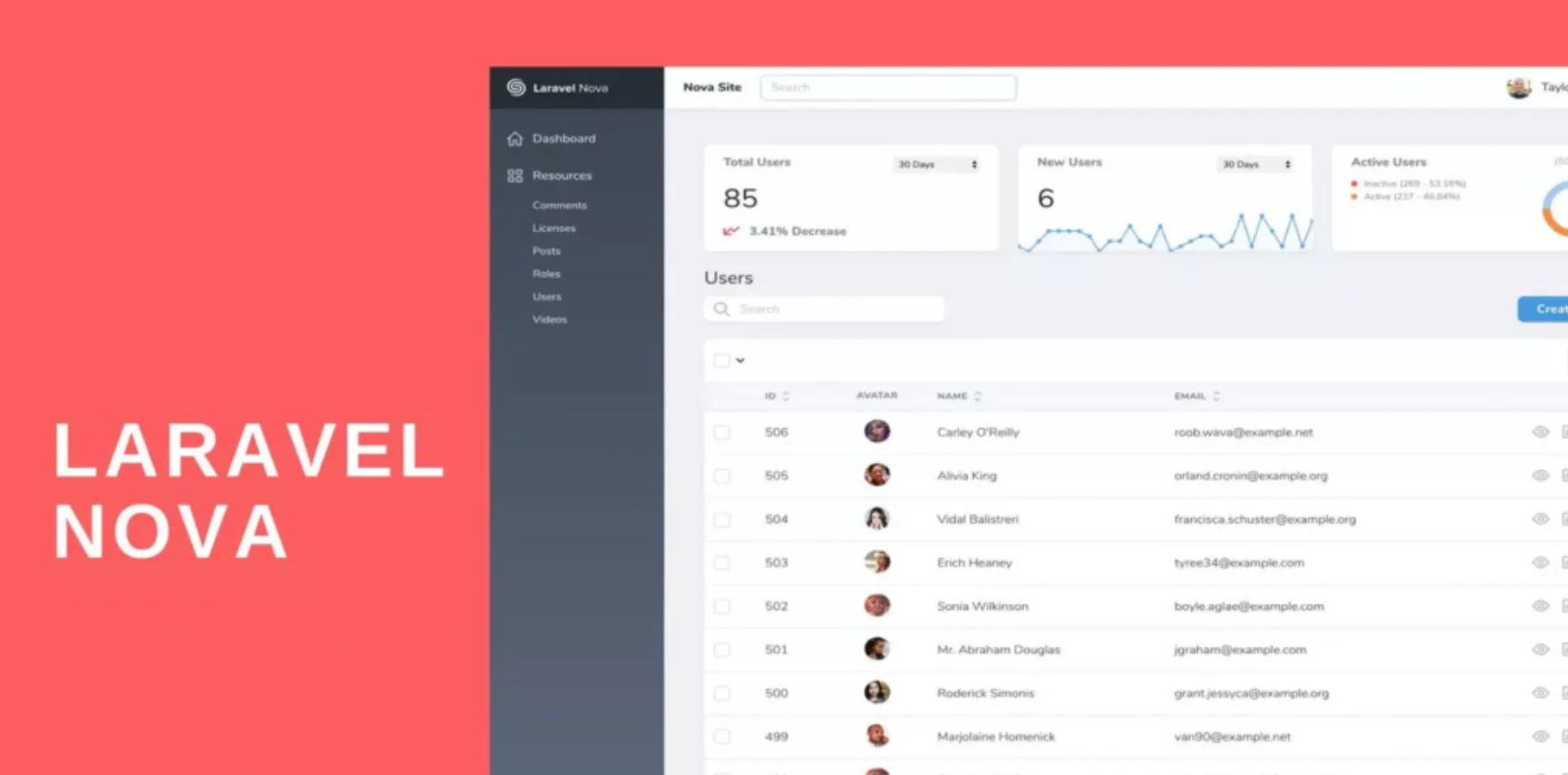
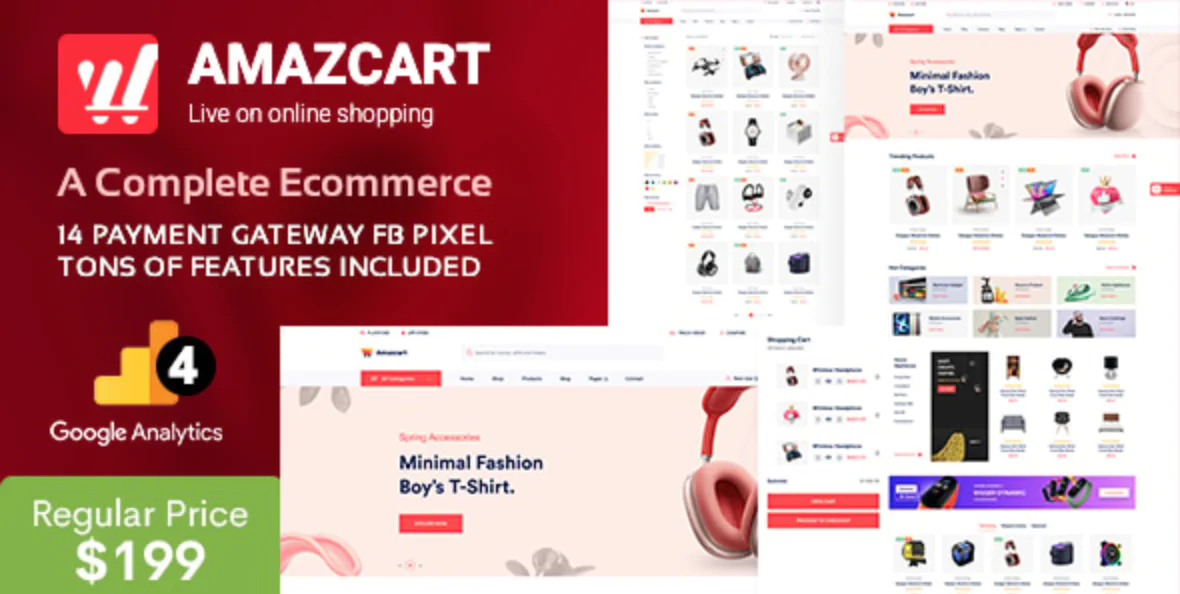
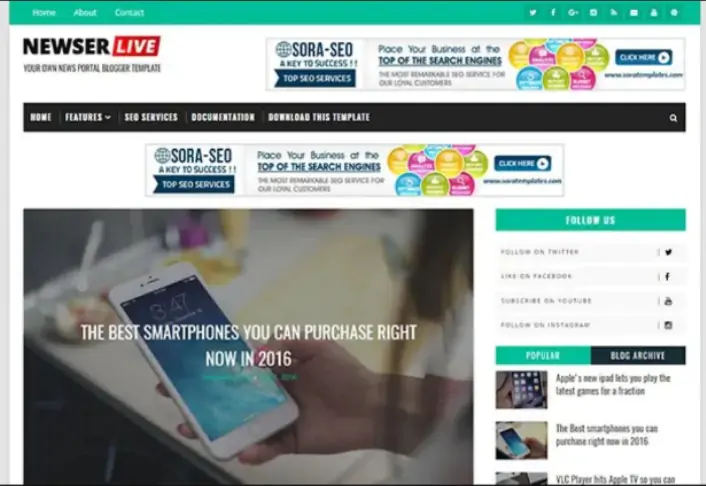
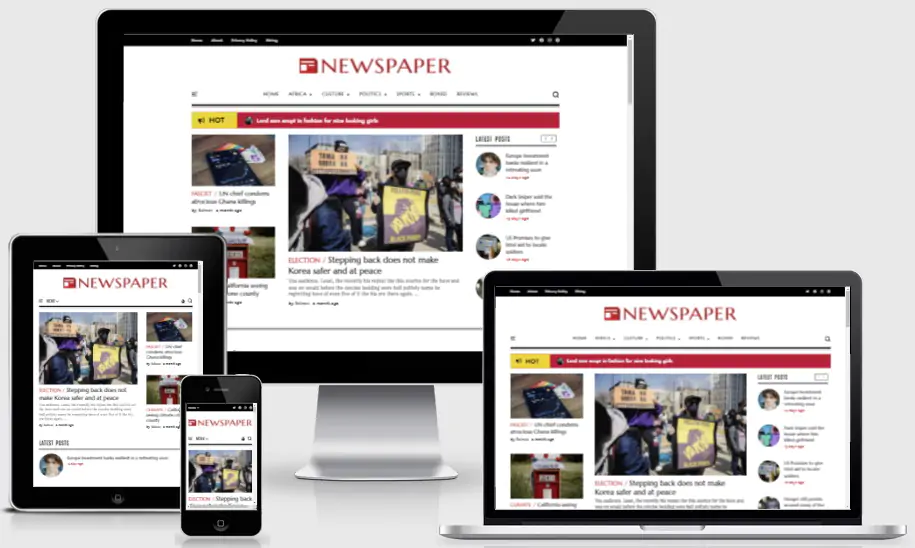
The 30 Best WordPress Themes for 2025: Free and Premium Options
Discover the 30 best WordPress themes, featuring top picks for blogs, eCommerce, portfolios, and more. Find free and premium themes with stunning designs, fast loading, and user-friendly features.
Read More...